The Best AI Answers To Questionnaires
Vera's AI finishes vendor questionnaires and compliance forms in minutes. It learns from your past assessments to deliver accurate, trusted answers — so your team can get back to selling, not spreadsheets.
200+ Sales, pre-sales, and security teams trust us to move faster
Escape Questionnaire Hell
Turn days of questionnaires into minutes. Upload your docs and let Vera auto-complete every response — no busywork, no delays.
10× Faster Completion
Finish lengthy vendor questionnaires in minutes, not days.
Describe your organization's data backup and disaster recovery procedures
No Hallucinations
Built-in safeguards ensure AI responses are grounded in your actual data and never make up false information.
What methods does your AI use to ensure confidence and provide accurate answers?
"Upload your company documents, security policies, and compliance certifications to enable AI-powered responses."
"Previous questionnaire responses that have been reviewed and approved by your team serve as training data for future responses."
"Our automation platform typically achieves 80% completion rates for new questionnaires after analyzing 2-3 similar historical responses."
What is the Coca-Cola secret recipe?
The AI does not have enough information to answer this question.
AI That Learns With Every Answer
AI improves automatically every time you manually edit or answer a response, getting smarter with each use.
Do you have SOC 2 Type II?
"No, but planned for Q3 2024"Mar 2024Do you have SOC 2 Type II?
"No, but planned for Q4 2024".AI Context uploaded.Jun 2024
Documents Uploaded
New SOC2 Policies.AI Context uploaded.Aug 2024
Do you have SOC 2 Type II?
"Yes, SOC 2 Type II certified"(Report attached)Nov 2024
Handles Any Question Format
Works with text responses, multiple choice, conditional logic, file uploads, and complex nested questions.
Which encryption standards do you currently use?
Questionnaire Automation features
Book a call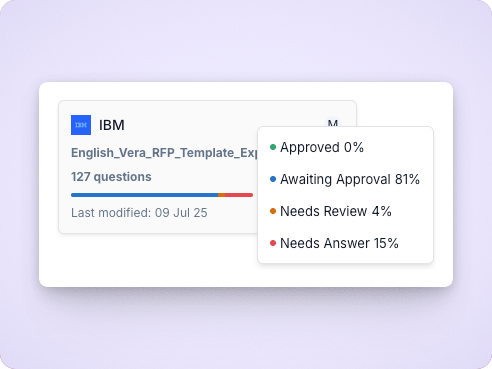
Reliable AI-powered responses
Generate accurate, contextual answers to security questions using advanced AI with built-in safeguards against hallucinations and confidence scoring.

Collaborative review workflows
Assign sections to subject matter experts, track progress, and gather approvals in real-time.

Knowledge base & policy sync
Build a knowledge base from past questionnaire responses and automatically sync the latest policy documents for accurate, up-to-date answers.

Multi-language responses
Support global customers with automated questionnaires in 59+ languages including Spanish, French, German, and more.

Export to original format (Beta)
Export completed questionnaire responses back to the original format while preserving formatting and structure.

Reporting
Track key metrics to manage workload, measure impact, and report ROI to leadership.
Start automating security questionnaires today
Join innovative teams who cut questionnaire time from days to minutes with AI-powered automation.
- Free 14-day trial
- No credit card required
- Setup in 5 minutes